If you are not running ADS active directory services on your windows 2012 server R2 server, you have probably noticed that there is no longer an easy way to configure your RDC SSL certificate in the remote desktop services configuration. I could not find good instructions to remedy this problem so the workgroup server would pass PCI compliance. If you use a workgroup local server self signed SSL certificate like yourserver.local you will get this PCI vulnerability warning: Microsoft Windows Remote Desktop Protocol Server Private Key Disclosure.
These are the easy and complete instructions for changing the RDC SSL certificate on your Windows 2012 server for TSL secure connections.
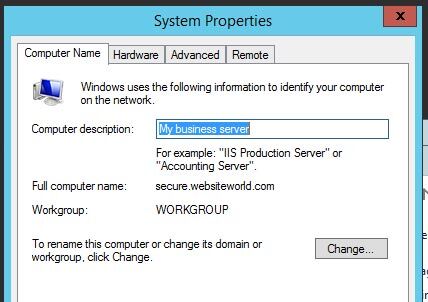
1) Your full computer name in your must match your SSL certificate name! In this case our SSL is secure.websiteworld.com so we have named our server secure.websiteworld.com
2) You need a .PFX export of your SSL certificate, make a note of the location you saved it, i.e. C:SSL
3) You can use this powershell script to install the certificate and make the process easier! Download the file, right click it, and run with Powershell. If you get confused about this part read this blog which explains in detail how to use the script.
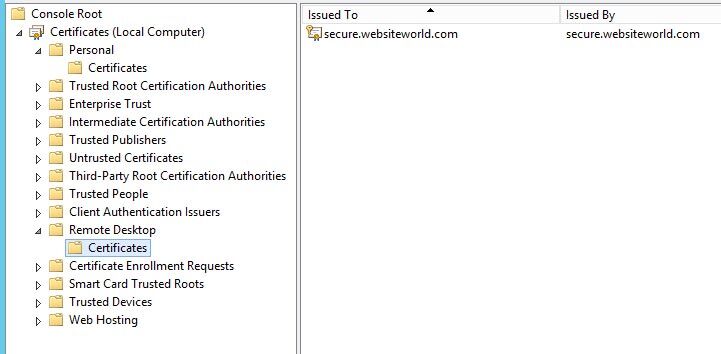
When you are finished you should be able to go back into your MMC.exe and the certificates snap in and see your remote desktop certificate there. If it is not there you can import it. You may also want to delete your .local old certificate. It should also be located under Personal/Certificates. If you have any issues, you can import the certificate into the personal/certificates and then start the powershell script in step 2 again. You can restart the server to make sure everything works and run your Trustwave scan or
Also a warning, make sure you have VNC or something on the server if you only have remote access to the server in case you get locked out!
Please Google +1 to help other people find this post!